“A riddle wrapped in a mystery inside an enigma.” That’s Winston Churchill describing Russia in 1939. The words puzzle and paradox have long been associated with annuities, marking them as one of the most difficult financial products to demystify. Recently, there has been a significant increase in annuity sales, which has added to the enigma. Why are they suddenly becoming so popular? Estate planning attorneys should know at least some basics.
The Original Annuity Riddle
The original annuity puzzle (the annuity market participation puzzle) refers to the economic paradox where retirees rarely choose to annuitize their wealth despite theoretical models suggesting this would be optimal for lifetime consumption smoothing and longevity risk protection. Classical economic theory, particularly as developed by Yaari (1965) (1), suggests that risk-averse individuals without strong bequest motives should convert a substantial portion of their wealth into lifetime annuities to hedge against outliving their assets; this optimizes their economic utility. They benefit from the insurance aspect of an annuity. Payouts are generally guaranteed for a lifetime, but the contract is priced according to average life expectancies.
However, in practice, voluntary annuity participation rates remain remarkably low across most developed countries. This discrepancy between theoretical predictions and observed behavior has sparked extensive research into potential explanations, including behavioral biases, bequest motives, concerns about healthcare costs, mistrust of insurance companies, desire for liquidity, existing annuities through Social Security and pensions, and the role of family risk-sharing.
The disinterest in annuities seems to be changing. Figure 1 shows a very recent trend of significantly increased annuity sales.

Figure 1: Growth in Annuity Sales Volume since 2004. Data from LIMRA. © wealthcarelawyer.com
The New Annuity Mystery – Why are Annuities Suddenly so Attractive?
There is no definitive answer. However, it is interesting that growth is driven almost exclusively by fixed annuities. A fixed annuity provides a guaranteed interest rate and principal protection since the insurance company bears the investment risk, but it typically offers lower potential returns with simpler features and lower fees. This maximizes the insurance aspect of an annuity.
In contrast, the returns of a variable annuity are tied to the performance of an investment portfolio chosen by the owner who bears the investment risk. These annuities offer higher potential returns and associated downside risk but with more complex features, higher management fees, and optional features like guaranteed income riders.
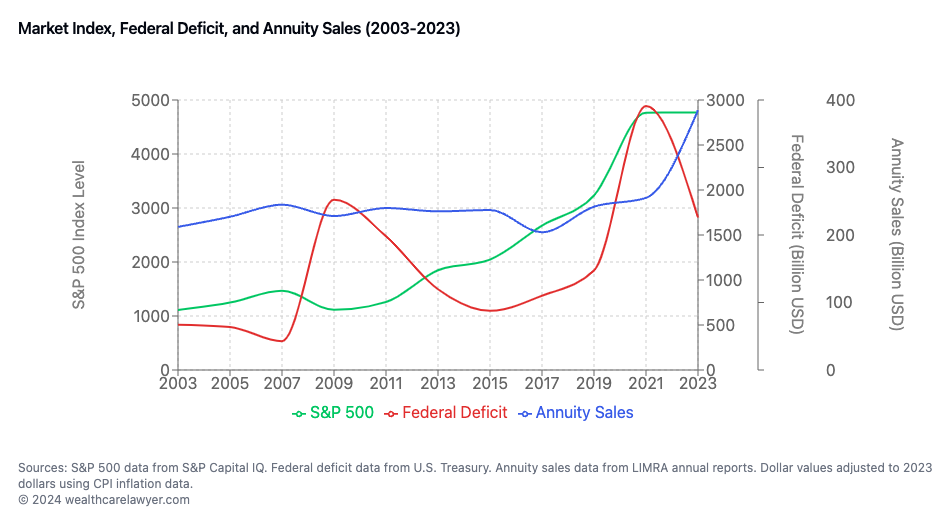
Figure 2: The most recent record federal deficit increase (red) seems to precede the increase in annuity sales. In contrast, good stock market performance should reduce the interest in annuities.
© wealthcarelawyer.com
Annuities are priced by calculating the present value of future payment obligations, adjusted for mortality risk, expenses, and profit margins. Insurance companies start with the principal investment and determine what payment stream they can provide based on current interest rates, actuarial tables (which predict how long they will need to make payments), their operating costs, and their desired profit margin. Higher interest rates generally allow for larger payments. In contrast, longer life expectancies, additional guarantee features, and higher expenses reduce the payment amounts the insurer can offer for a given principal investment.
In the first quarter of 2024, annuity sales reached a record $113.5 billion, marking the highest first-quarter sales figure in the 40-year history of Limra’s data tracking. While it is unclear what caused the sudden increase in the popularity of annuities, we believe that concern for the viability of Social Security because of the ballooning deficit may have contributed to it. LIMRA offers an alternative evaluation:
“Favorable economic conditions and demographic shifts have driven demand for investment protection and guaranteed lifetime income solutions that are unique to annuity products. During their discussion, Hodgens focused on the economic factors, such as higher interest rates and prolonged market volatility, which have enhanced the value and appeal of fixed annuity products, particularly fixed-rate deferred (FRD) and fixed indexed annuities (FIA).” (2).
It is also possible that current affluent baby boomers, as the sandwich generation, see value in diversifying with annuities: The annuity is considered spending money to help assure a certain standard of living, while investments are invaded only sparingly to allow for a growing legacy for the next generation. A guaranteed income stream from an annuity can provide psychological permission for retirees to spend more freely on themselves. Without an annuity, many retirees tend to be overly conservative with spending, worried about depleting their savings too quickly or not having enough for longevity and emergencies.
The Annuity Product Enigma
In an effort to make annuities more attractive, the industry has developed numerous products that address various concerns and preferences clients may have. As a general rule, many of the special flavors partially defeat the economic purpose of an annuity, which is utility maximization for persons without a strong bequest motive.
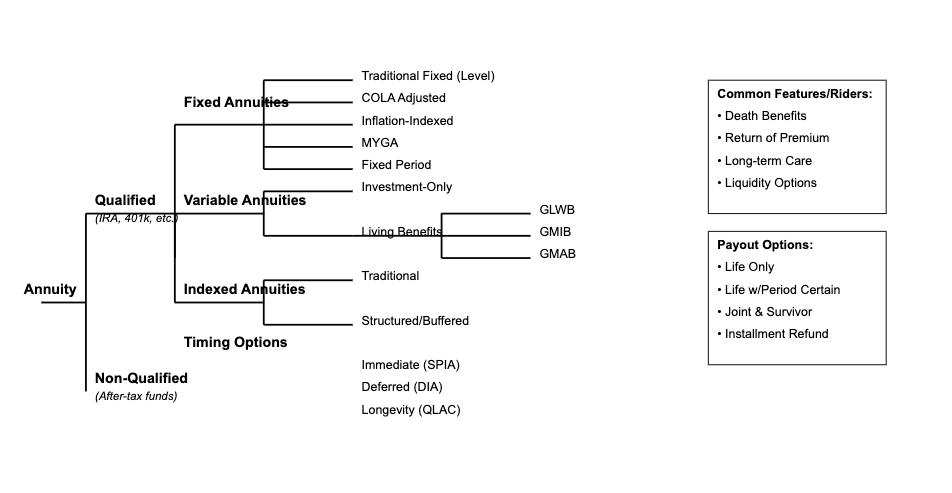
Figure 3: Some of the major annuity families and species. © wealthcarelawyer.com
Annuity contracts have evolved from basic guaranteed income instruments into complex financial products, each structured to address specific risk-transfer and income objectives. This evolution has produced three distinct primary classifications: Fixed, Variable, and Indexed annuities.
Fixed Annuities represent the foundational form. The Single Premium Immediate Annuity (SPIA) facilitates direct risk transfer through immediate income guarantees, leveraging mortality credits to enhance returns. Deferred Income Annuities (DIAs) modify this framework by introducing a time delay element, optimizing for future income maximization. Qualified Longevity Annuity Contracts (QLACs) emerged as a specialized adaptation to retirement account regulations, permitting Required Minimum Distribution deferral to age 85, subject to statutory limitations ($200,000). Multi-Year Guaranteed Annuities (MYGAs) provide fixed-rate guarantees over specified periods, offering liquidity features absent in traditional fixed annuities.
Variable Annuities evolved to incorporate market exposure through separate account structures. The basic Investment-Only variant provides tax-deferred market participation, while Living Benefit riders introduced protective features:
- Guaranteed Lifetime Withdrawal Benefits (GLWB) ensure sustained withdrawal rates
- Guaranteed Minimum Income Benefits (GMIB) protect future income bases
- Guaranteed Minimum Accumulation Benefits (GMAB) provide principal protection parameters
Indexed Annuities represent a hybrid development, linking returns to market indices while maintaining principal protection. Structured/Buffered variants modify this framework by accepting defined downside exposure in exchange for enhanced participation rates.
Tax treatment bifurcates between:
- Qualified: Pre-tax funding, full distribution taxation
- Non-Qualified: After-tax funding, exclusion ratio calculations
Contract modifications across all variants may include:
- Mortality benefit enhancements
- Inflation adjustment mechanisms
- Long-term care provisions
- Premium return options
- Distribution structure alternatives
This taxonomic framework provides the foundation for analyzing suitability, tax implications, and regulatory considerations across various client objectives and constraints.
Client Self Help
More information about annuities is not necessarily more helpful to consumers: “More complete, and therefore more complex information about annuity products leads to reduced attention and produces worse consumer choices. In an eye-tracking experiment comparing consumer response to a real, relatively brief annuity brochure and an edited and shortened version of the same brochure, we find that the more complex the materials, the faster attention declines.” (3).
This underscores the need for a learned intermediary to digest the information and to tailor it to the individual’s needs, preferences, and financial situation, who can ask clarifying questions to ascertain understanding.
Given a certain contract amount and their ages, many clients want to know what monthly or annual income they can expect given the current rate structures. The Annuity Calculator by annuity.org promises to do that. Others, such as Schwab, have similar annuity calculators, and results may differ.
How to Help Your Estate Planning Clients
The increasing complexity and popularity of annuity products present both opportunities and challenges for estate planning attorneys. Given the recent surge in annuity sales and evolving product complexity, attorneys must establish clear parameters for client discussions regarding these financial instruments.
Estate planning attorneys can appropriately address annuities by maintaining strict professional boundaries while providing valuable guidance. The fundamental framework involves three key components: permissible discussion parameters, professional referral protocols, and risk management considerations.
Permissible Discussion Parameters: Estate planning attorneys may appropriately discuss the theoretical foundations of annuities, including their role in consumption smoothing and longevity risk protection as established in classical economic theory. Discussions may encompass general tax implications, basic product classifications (fixed, variable, and indexed), and integration with estate planning objectives.
Professional Referral Protocols: Given the product complexity illustrated in the annuity taxonomy, specific product recommendations should be deferred to qualified specialists. Appropriate referral channels include:
- Independent Annuity Brokers
- Independent Insurance Advisors
- Certified Financial Planners (CFPs)
- Chartered Life Underwriters (CLUs)
Risk Management Considerations Documentation protocols should include:
- Contemporaneous recording of annuity-related discussions
- Specific referral documentation
- Clear delineation of scope limitations regarding product recommendations
The attorney’s role should focus on identifying how annuity contracts may integrate with broader estate planning objectives while ensuring clients receive specialized guidance for product selection. This approach aligns with the current market dynamics where product complexity demands specialized expertise beyond the scope of general estate planning practice.
Professional network development should emphasize relationships with independent advisors who maintain appropriate licensing and demonstrate expertise in the evolving annuity marketplace. This network enables appropriate delegation of product-specific guidance while maintaining the attorney’s role in the overall estate planning strategy.
This framework enables estate planning attorneys to address the increasing relevance of annuity products while maintaining appropriate professional boundaries and ensuring clients receive comprehensive guidance from qualified specialists regarding specific product selection and implementation.
Podcast
References
- Yaari, M.E., 1965. Uncertain lifetime, life insurance, and the theory of the consumer. The Review of Economic Studies, 32(2), pp.137-150.
- LIMRA, Building on the Record Annuity Sales Momentum, LIMRA (May 22, 2024), https://www.limra.com/en/newsroom/industry-trends/2024/building-on-the-record-annuity-sales-momentum/.
- Harvey, Joseph, John G. Lynch, Philip Fernbach, and Ji Hoon Jhang. “Information Overload in Consumer Response to Annuities: Eye-Tracking and Behavioral Evidence.” Consumer Financial Protection Bureau Office of Research Working Paper 23-01 (2023).
https://papers.ssrn.com/sol3/Delivery.cfm?abstractid=4394792
Further reading focused on Income Annuities
- LIMRA. (2024, May 22). First Quarter U.S. Annuity Sales Mark 14th Consecutive Quarter of Growth. Retrieved from https://www.limra.com/en/newsroom/news-releases/2024/limra-first-quarter-u.s.-annuity-sales-mark-14th-consecutive-quarter-of-growth/
- Fidelity Investments. (2023, June 5). Understanding Annuities. Retrieved from https://www.fidelity.com/learning-center/personal-finance/retirement/what-is-an-annuity
- Williams, R. (2023, April 12). The Case for Income Annuities When Rates Are Up. Retrieved from https://www.schwab.com/learn/story/case-income-annuities-when-rates-are-up
- Institute of Business and Finance. (2023, January). Certified Annuity Specialist Course Materials.
- Financial Industry Regulatory Authority. (2022, July 15). Deferred Income Annuities: Plan Now for Payout Later. Retrieved from https://www.finra.org/investors/insights/deferred-income-annuities
- Pfau, W. (2020, May 5). Income Annuities: The Guaranteed Stream Of Income In Retirement. Retrieved from https://www.forbes.com/sites/wadepfau/2020/05/05/income-annuities-the-guaranteed-stream-of-income-in-retirement/?sh=1f05b93e5143
- Kitces, M. (2015, April 1). Understanding The Role Of Mortality Credits – Why Immediate Annuities Beat Bond Ladders For Retirement Income. Retrieved from https://www.kitces.com/blog/understanding-the-role-of-mortality-credits-why-immediate-annuities-beat-bond-ladders-for-retirement-income/
- Cruz, H. (2005, July 24). Lifetime Income Benefit Rider vs. Annuitization. Retrieved from https://www.chicagotribune.com/news/ct-xpm-2005-07-24-0507240025-story.html
- Pfau, W. (n.d.). What Is a Safety-First Retirement Plan? Retrieved from https://retirementresearcher.com/what-is-a-safety-first-retirement-plan/
Like this:
Like Loading...









![The Rise of Annuities – A Riddle Wrapped in a Mystery Inside an Enigma? [Podcast]](https://i0.wp.com/nationallawforum.com/wp-content/uploads/2024/11/Estate-Planning-Wills-Trusts-Magnifying-Glass.jpg?resize=825%2C510&ssl=1)
